TeleMessage, the company behind the modified Signal client used by Trump admin officials, has been breached.
Attacker claims the hack took "15-20 minutes" with minimal effort.
TeleMessage creates modified versions of Signal/WhatsApp/Telegram that archive messages for gov agencies.
Recently made headlines when National Security Advisor Waltz was photographed using it.
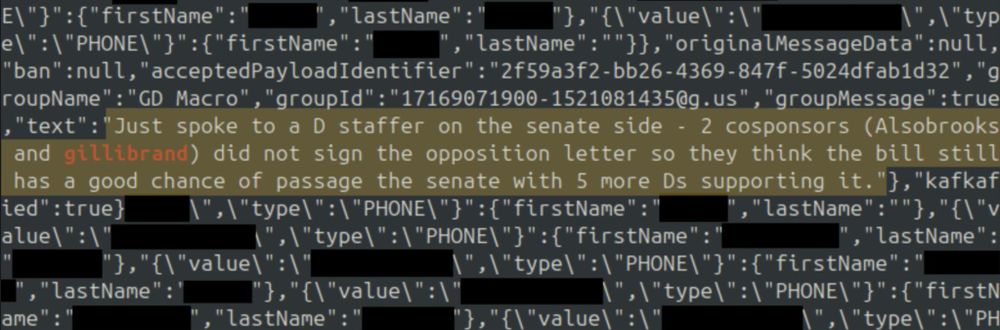
A hacker accessed unencrypted message contents, contact info of gov officials, admin credentials, and customer data.
Notably includes CBP, Coinbase, and other financial institutions.
This confirms security researchers' warnings: Adding message archiving to E2EE apps fundamentally breaks their security model by creating a vulnerable "man-in-the-middle" point.
May 5, 2025 18:21
One screenshot showed 747 CBP officials in the system.
Data includes fragments of live communications, including sensitive discussions about pending crypto legislation.
Incident validates Signal's previous statement that they "cannot guarantee security properties of unofficial versions."
TeleMessage's claims about maintaining Signal's security were demonstrably false.
Worth noting: While cabinet members' messages weren't accessed, the trivial nature of the breach suggests more data could have been exposed if attacker chose to dig deeper.
TeleMessage has wiped their website. (All links on the page are dead ends)
Multiple gov agencies including State Dept and CDC have active contracts with the company.
There is no such thing as a backdoor only for the "good guys"
You can't have it both ways - either messages are truly E2EE or they're not.
Thanks 404media for this awesome reporting as usual:
www.404media.co/the-...
The Signal Clone the Trump Admin Uses Was Hacked
TeleMessage, a company that makes a modified version of Signal that archives messages for government agencies, was hacked.