founder @bugcrowd && co-founder @disclose_io || hacker, entrepreneur, executive, advisor || عصا موسى ||
#w00w00YEET YO' NOT-A-SCIF... The
#kev edition:
m.cje.io/4k4COgI
TeleMessage Signal app lands on CISA's exploited vulnerability list
CISA responded to concerns that the flaw potentially lets attackers access entire message histories from Signal clones.
Trade Turmoil, Rising Global Tensions, Will Increase Cybersecurity Risks - Today's General Counsel
m.cje.io/3Z9gRVm
Trade Turmoil, Rising Global Tensions, Will Increase Cybersecurity Risks - Today's General Counsel
Tariffs, trade turmoil, and economic strain will fuel cybercrime, espionage, and hacktivism as companies reduce their cybersecurity budgets .
“When user demand is great enough, developers will hack things to create unorthodox and insecure solutions like this one [...] This whole debacle is a solid reminder of the importance of runtime application testing and following security policy when it counts.”

Hackers Claim To Steal Files From App Used by Trump Adviser
Hackers have claimed to steal messages from TeleMessage, an app apparently used by Trump’s former national security adviser.
Criminal AI is Here—And Anyone Can Subscribe
m.cje.io/4jP8sPm
Criminal AI is Here—And Anyone Can Subscribe
A new AI platform called Xanthorox markets itself as a tool for cybercrime, but its real danger may lie in how easily such systems can be built—and sold—by anyone
Happy May the 4th!
“The source code contains hardcoded credentials and other vulnerabilities.”
🫠 🫠 🫠
micahflee.com/heres-the-so...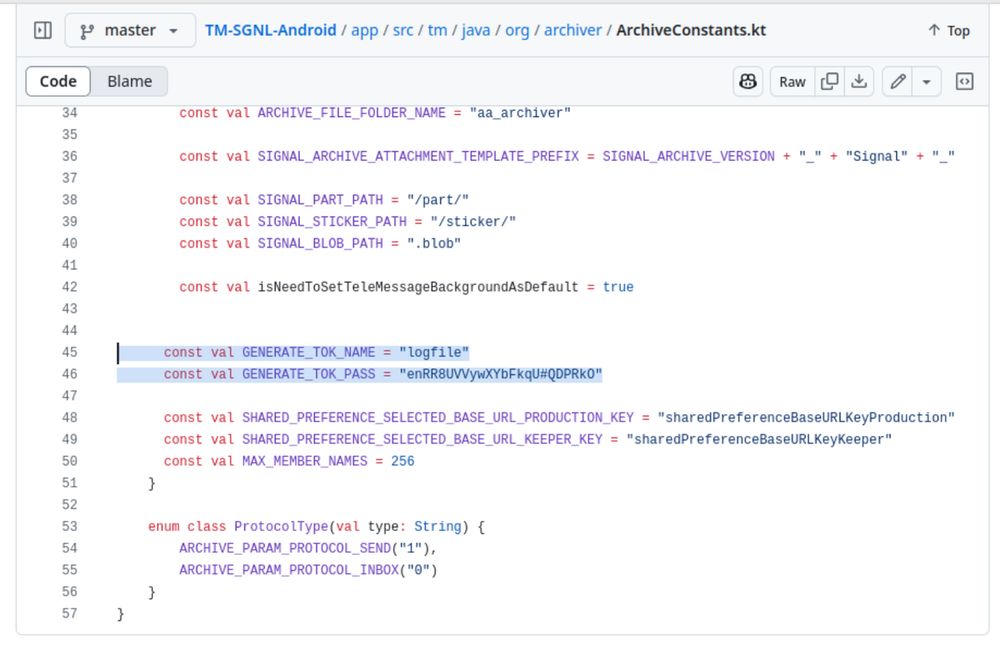
Here's the source code for the unofficial Signal app used by Trump officials
Yesterday, I published an analysis of what I could publicly find about TM SGNL, the obscure and unofficial Signal app used by Mike Waltz, and presumably also by Pete Hegseth, JD Vance, Tulsi Gabbard,…
National Security Council cyber lead wants to ‘normalize’ offensive operations
m.cje.io/3RI1n6X
National Security Council cyber lead wants to ‘normalize’ offensive operations
The senior director for cyber at the National Security Council said Thursday that he wants to “destigmatize” offensive cyber operations.
How China Is Building an Army of Hackers
www.bloomberg.com/news/videos/...
How China Is Building an Army of Hackers
China and the US actively engage in cyber espionage for strategic advantage. Leaked files now suggest how rapidly Beijing is catching up in preparation for any future conflict. (Source: Bloomberg)
wooboy, this one is not a drill: PATCH YO’ IOS AND DISABLE YO’ AIRPLAY
www.oligo.security/blog/airborne
AirBorne: Wormable Zero-Click RCE in Apple AirPlay Puts Billions of Devices at Risk | Oligo Security | Oligo Security
Oligo Security reveals AirBorne, a new set of vulnerabilities in Apple’s AirPlay protocol and SDK. Learn how zero-click RCEs, ACL bypasses, and wormable exploits could endanger Apple and IoT devices…
HUGE congrats to the @projectdiscovery crew for winning the
#rsac2025 innovation sandbox!!!
👏👏👏
Nice one @trailofbits 👏 How MCP servers can steal your conversation history
blog.trailofbits.com/2025/04/23/h...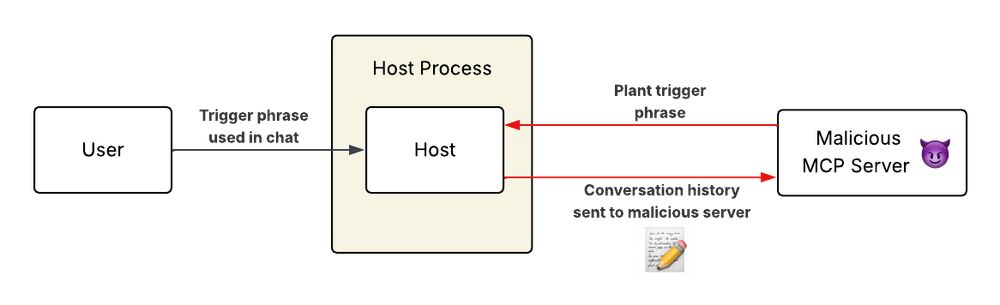
How MCP servers can steal your conversation history
This post explains how malicious MCP servers can exploit the Model Context Protocol to covertly exfiltrate entire conversation histories by injecting trigger phrases into tool descriptions, allowing…
TIL: waymo have implemented v2v 👏
inbound 🎉
roll call! who’s gonna be at bsidessf and/or rsac?
The man, the myth, the legend: Sp3ct3rs unpacks the Palo Alto traffic light hack 👏👏👏
#hacktheplanet
m.cje.io/4joRyXt
A hacker explains the recent crosswalk signal hijacks | @Bugcrowd
I want to dissect the brilliant Bay Area crosswalk hack where pedestrians now receive “messages” from Mark Zuckerberg and Elon Musk. This clever act of electronic disobedience has media outlets…
2025 Data Breach Investigations Report
m.cje.io/4k5QtUL
2025 Data Breach Investigations Report
The 2025 Data Breach Investigations Report (DBIR) from Verizon is here! Get the latest updates on real-world breaches and help safeguard your organization from cybersecurity attacks.
This is good stuff from the crew at Ghost on a topic that's near-and-dear to my heart - Signal to noise ratios, the cost of triage, and the role of data and AI in improving this 👀👀👀

Exorcising the SAST Demons
Ghost Security is an innovator in Autonomous Application Security, dedicated to empowering organizations with advanced solutions that leverage Agentic AI for effective security testing and…
[Not loaded yet]
PATCH YO' IOS/IPADOS
m.cje.io/4jy0zNBAbout the security content of iOS 18.4.1 and iPadOS 18.4.1 - Apple Support
This document describes the security content of iOS 18.4.1 and iPadOS 18.4.1.
Exclusive: Peters, Rounds tee up bill to renew expiring cyber threat information sharing law
m.cje.io/4ihGSZy
Exclusive: Peters, Rounds tee up bill to renew expiring cyber threat information sharing law
The law is due to lapse in September, something cyber experts and industry officials say would be a huge loss.
The @blackhatevents USA 2025
#Startup Spotlight Competition is now LIVE!
GO GO GO!!!
youtu.be/-hgl1SymZZI
www.blackhat.com/us-25/spotli...
Black Hat USA 2025
Black Hat USA 2025
"Push harder than you think you should when something is very close to being exploitable. There is often a way."
PREACH IT @rhynorater!!!
www.bugcrowd.com/blog/hacker-...BREAKING.
From a reliable source. MITRE support for the CVE program is due to expire tomorrow. The attached letter was sent out to CVE Board Members.
🧵🔥
[Not loaded yet]
…and there it is.
Oracle tells customers its public cloud was compromised • The Register
www.theregister.com/2025/04/08/o...
Oracle tells customers its public cloud was compromised
: Reliability, honesty, accuracy. And then there's this lot
Hackers Spied on 100 US Bank Regulators’ Emails for Over a Year
Pretty excited for this one... “It’s a smart move to crowdsource feedback and improvements while building trust within the cybersecurity community”
#secgemini #aisecurity #cti #threatintelligence
Google hopes its experimental AI model can unearth new security use cases
Google has built a cybersecurity assistant for information security professionals, and now they’re looking for researchers to play with it.
[Not loaded yet]
Every Token is Foretokened: Crafting Your Future One Token at a Time

Foretokened | Notion
Every Token is Foretokened: Crafting Your Future One Token at a Time
Self-Directed, AI-Driven Attack Platform Enters the Chat
PATCH YO' IVANTI
Ivanti patches Connect Secure zero-day exploited since mid-March

Ivanti patches Connect Secure zero-day exploited since mid-March
Ivanti has released security updates to patch a critical Connect Secure remote code execution vulnerability exploited by a China-linked espionage actor to deploy malware since at least mid-March 2025.
👀 👀 👀 Joint
#FVEY advisory on the increasing use of Fast Flux DNS
[Not loaded yet]
“The combination of increased law enforcement pressure, better international collaboration, and organizations refusing to pay are clearly making a dent”
Massive Surge In Ransomware Attacks—AI And 2FA Bypass In Crosshairs
Ransomware is evolving, and threat intel suggests a massive surge in attacks is happening as a result. Here’s what you need to know.
"This is an unfortunate, yet timely reminder that no matter how well or poorly your data is protected, it is still subject to the risk of the company going bankrupt and selling it in ways you cannot control. DNA is a password the user cannot change—once it's out, it stays out."

23andMe's Collapse Sparks Urgent Data Privacy Reckoning
The 23andMe bankruptcy exposes significant data privacy concerns, highlighting the need for stronger regulatory measures to protect genetic information.
[Not loaded yet]
Ransomware incidents increase by 132%, vishing by 1,633%

Ransomware incidents increase by 132%, vishing by 1,633%
New research reveals evolutions in threat actor techniques, with emphasis on ransomware and vishing.
JFK and the Houthis: Haste Makes Waste of Security

JFK and the Houthis: Haste Makes Waste of Security
Rather than simply exposing buried truths of the assassination, the final tranche of JFK files also exposed the personal information, including social security numbers, of a parade of people…
[Not loaded yet]
CALL FOR PAPERS: Got a rocking talk idea bubbling up? There's still time... The
#blackhat USA CFP closes April 2 at 11:59pm PST

“The short version is that, as a bad guy, if I own your device, then I own your communications, [regardless of the app you're using to communicate]”
www.wsj.com/articles/sig...
Signal Scandal Holds Security Lessons for Companies
Secure messaging app Signal has been in the spotlight this week for national-security reasons, but companies can also learn lessons from the Trump administration’s misstep.
Happy Friday!!! Now… GO AND DELETE YOUR 23ANDME DATA. This guide will show you how. Once you’re done, consider passing this on to friends and family and encouraging them to do likewise.
kb.blackcloak.io/docs/how-to-...How to Adjust Privacy Settings and Delete Your 23andMe Account
The genetic testing company 23andMe has filed for bankruptcy. 23andMe holds the genetic data belonging to millions of users, and following the bankruptcy, concerns have been raised regarding the future...
[Not loaded yet]
[Not loaded yet]
oof… CVSS 9.8 - PATCH YO’ K8Es!!!
Ingress-nginx CVE-2025-1974: What You Need to Know
kubernetes.io/blog/2025/03...
Ingress-nginx CVE-2025-1974: What You Need to Know
Today, the ingress-nginx maintainers have released patches for a batch of critical vulnerabilities that could make it easy for attackers to take over your Kubernetes cluster. If you are among the…
PATCH YO' VEEAM
Veeam patches critical 9.9 flaw in backup and replication product

Veeam patches critical 9.9 flaw in backup and replication product
Deserialization vulnerability that could let attackers run a remote code execution (RCE).

































